Since March this year (2023), Github has started to force users to enable two-step verification 2FA (two-factor) login verification, undoubtedly for security reasons, after all, once a Github account is stolen, all code repositories will be destroyed. For the necessity of two-factor login, please refer to: Don\'t let your server (vps) become a botnet (ssh brute force crack), key verification and two-way factor login are worth having.
In simple terms, two-factor login is a measure to prove "you are yourself" through a third-party device. Github officially recommends downloading 1Password, Authy, Microsoft Authenticator and other APPs on the mobile side to verify by scanning the code. In fact, it is not so troublesome. This time we will implement two-factor login verification through Python/Golang code.
TOTP algorithm
Time-based One-Time Password (TOTP) is a time-based one-time password algorithm used to enhance identity authentication security.
TOTP is based on the HMAC (Hash-based Message Authentication Code) algorithm and timestamp to generate one-time passwords. The user and server share a secret key, usually exchanged during initial authentication. Based on this key, the server generates an initial value for verification.
At each time step (usually 30 seconds), based on the current timestamp and shared secret key, an HMAC algorithm is used to generate a hash value. Then, a dynamic password of fixed length is extracted from the hash value. This dynamic password is valid within the set time step, after which it will automatically expire.
When authenticating, the user needs to enter the dynamic password generated within the current time step. The server will use the same algorithm and shared secret key to verify that the password provided by the user matches. Since the dynamic password expires after the time step expires, even if intercepted, it cannot be reused in the next time step.
TOTP is widely used in the implementation of two-factor authentication (2FA) and multi-factor authentication (MFA). By combining the user's password and dynamically generated passwords each time, TOTP provides an extra layer of security protection and effectively reduces the risk of passwords being stolen or guessed.
Common TOTP applications include Google Authenticator and Authy authentication apps that generate TOTP algorithm based dynamic passwords and bind them to the user's online accounts to provide more secure login.
In short, it is a key with a lifespan. After 30 seconds, this key will expire. The client and server share a key to verify the validity of the key through the HMAC algorithm.
TOTP algorithm implementation (Python3.10)
First, a key should be generated on the server side, which is shared between the client and the authentication server. The key can be a string, but Github officially turned this key into a QR code for easy mobile scanning and verification. Open your Github account, select Settings -> Two-step verification:
Click the green button and select Enable two-step verification.
At this point, the system will automatically generate a QR code, which is the shared key:
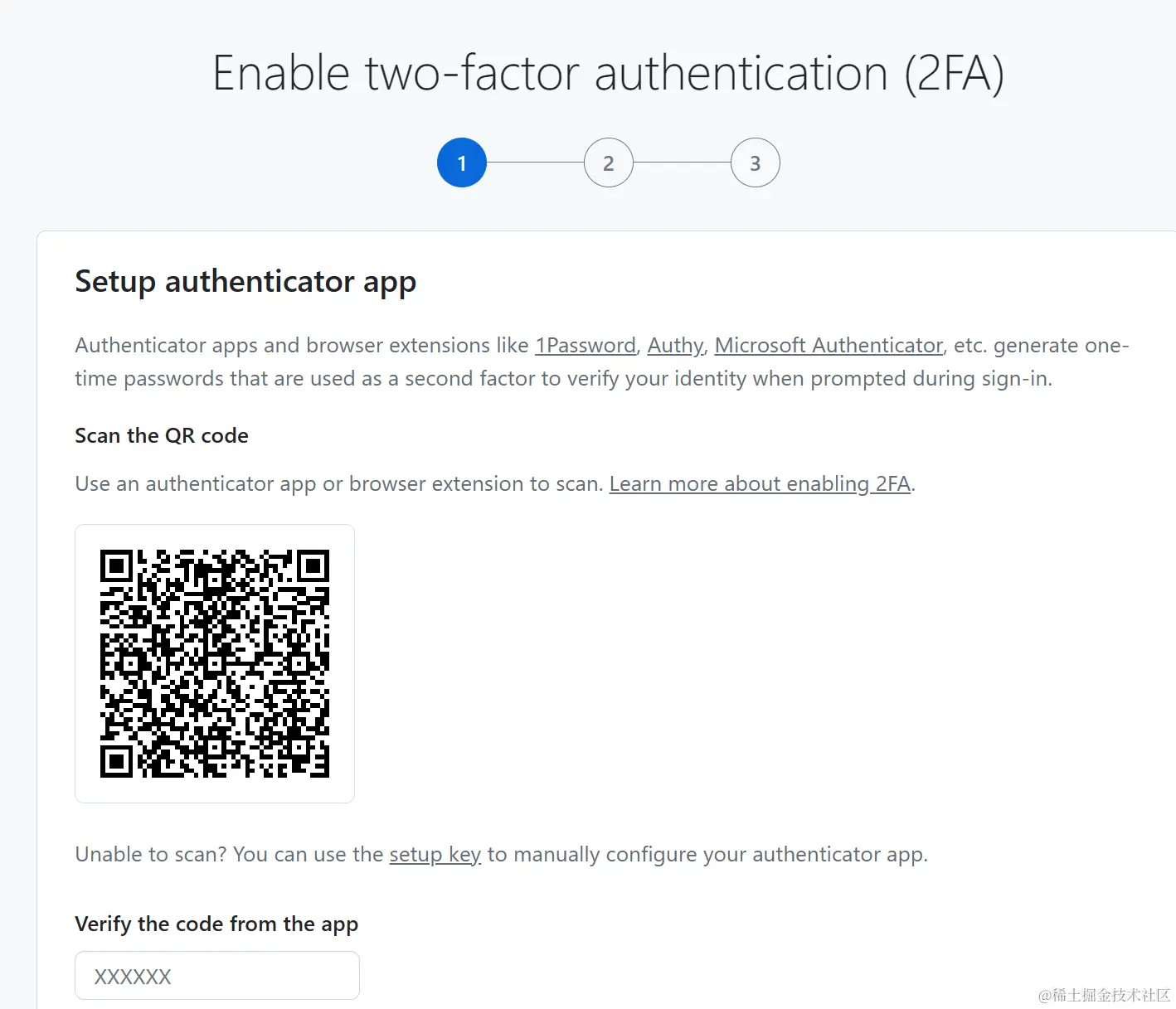
The string form of the key can be obtained by clicking the setup key link.
After getting the system key, we install the TOTP library based on Python:
$ pip3 install pyotp
Then write the code to generate the current sequential verification code:
import pyotp
import time
# Set server secret key
secret_key = "Key generated by Github server (ie QR code)"
# Create a TOTP object using the secret key and time interval (default 30 seconds)
totp = pyotp.TOTP(secret_key)
# Generate current OTP
current_otp = totp.now()
print(f"Current OTP: {current_otp}")
Running result:
$ python -u test_totp.py
Current OTP: 809888
You can see that based on the key we generate a verification code valid within 30 seconds. Then fill in this verification code in the Verify the code from the app text box on the page. It's simple and convenient, and there's no need for mobile participation.
Implement TOTP algorithm with Golang1.21
If the client language is Golang, TOTP algorithm can also be easily implemented. First make sure Golang1.18 is installed locally, here we use the latest Golang1.21:
$ go version
go version go1.21.1 windows/amd64
Then install the corresponding totp package via go get:
$ go get github.com/pquerna/otp
$ go get github.com/pquerna/otp/totp
Then write the main.go entry code file:
package main
import (
"encoding/base32"
"fmt"
"time"
"github.com/pquerna/otp"
"github.com/pquerna/otp/totp"
)
// Demo function, not used in main
// Generates Passcode using a UTF-8 (not base32) secret and custom parameters
func GeneratePassCode(utf8string string) string {
secret := base32.StdEncoding.EncodeToString([]byte(utf8string))
passcode, err := totp.GenerateCodeCustom(secret, time.Now(), totp.ValidateOpts{
Period: 30,
Skew: 1,
Digits: otp.DigitsSix,
Algorithm: otp.AlgorithmSHA512,
})
if err != nil {
panic(err)
}
return passcode
}
func main() {
passcode := GeneratePassCode("Key generated by Github official")
fmt.Print(passcode)
}
Here the verification code is generated through the GeneratePassCode function. The default validity period is still 30 seconds, and the algorithm is based on otp.AlgorithmSHA512.
Running result:
$ go run main.go
692540
Then fill in this verification code in the Verify the code from the app text box on the page. Unlike Python, Golang can run directly on any platform after compilation, which is theoretically much more convenient than Python.
Conclusion
In general, GitHub's two-factor login provides higher account security and protects users from unauthorized access and potential data breaches. It is a simple and effective security measure that is worth taking to protect GitHub accounts and related code assets. However, Github officially promotes the paid 1Password software, which should have some interest ties, but for those of us who can code, this is not a problem.
Comments